Table of Contents
- The Command Line Tool
- The PHP, Ruby and Python Extensions
- Cloud and Browser Based Signing
MyPDFSigner provides extensions for PHP, Ruby and Python. The extensions are only available for Linux. Please contact KryptoKoder if you need extensions for a different OS.
Install the PHP|Ruby|Python extension (Fedora|Ubuntu):
$ sudo dnf install mypdfsigner-[php|ruby|python]-3.1.5-1.x86_64.rpm
$ sudo gdebi mypdfsigner-[php|ruby|python]_3.1.5-1_amd64.deb
Test a script from the command line:
$ [php|ruby|python] /usr/local/mypdfsigner/tests/test.[php|rb|py]
Check /tmp/example-signed-[php|ruby|python].pdf.
There are further examples in the /usr/local/mypdfsigner/tests/ directory. The test-json.[php|rb|py] example shows how to use json notation to build a configuration file on the fly, and the test-external.[php|rb|py] examples shows how to sign a PDF by having a signature created as an external step, possibly by a remote third party application.
You can also quickly play with the MyPDFSigner extensions in a Docker container by running the kryptokoder/mypdfsigner-[php|python-ruby]:latest image as shown below.
PS C:\> dir .\docker-demo\
Directory: C:\docker-demo
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 15-Feb-21 6:03 PM 196769 example-signed.pdf
PS C:\> docker run -v C:\docker-demo:/tmp -it kryptokoder/mypdfsigner-php:latest /bin/bash
root@d06baeb4a296:/# php /usr/local/mypdfsigner/tests/test.php
0#Document signed
0#Document signature verified [Signer: MyPDFSigner Test]
root@d06baeb4a296:/# exit
exit
PS C:\> docker run -v C:\docker-demo:/tmp -it kryptokoder/mypdfsigner-python:latest /bin/bash
root@de911130db8a:/# python3 /usr/local/mypdfsigner/tests/test.py
0#Document signed
0#Document signature verified [Signer: MyPDFSigner Test]
root@de911130db8a:/# exit
exit
PS C:\> docker run -v C:\docker-demo:/tmp -it kryptokoder/mypdfsigner-ruby:latest /bin/bash
root@a2cc80b8f060:/# ruby /usr/local/mypdfsigner/tests/test.rb
0#Document signed
0#Document signature verified [Signer: MyPDFSigner Test]
root@a2cc80b8f060:/# exit
exit
PS C:\> dir .\docker-demo\
Directory: C:\docker-demo
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 15-Feb-21 6:10 PM 196958 example-signed-php.pdf
-a---- 15-Feb-21 6:11 PM 196976 example-signed-python.pdf
-a---- 15-Feb-21 6:11 PM 196965 example-signed-ruby.pdf
-a---- 15-Feb-21 6:03 PM 196769 example-signed.pdf
PS C:\>
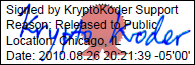
The list of functions provided by MtPDFSigner is shown below. Depending on the scripting language used they should be prepended either with mypdfsigner. or mypdfsigner_. The arguments, which are self explanatory, are always strings, except for visible, certify and timestamp, which are boolean. The return values are strings, that can be tokenized to retrieve values that may be fed into other functions.
get_signer_info(conffile)
sign(input, output, password, location, reason, visible, certify, timestamp, conffile)
add_metadata_sign(input, output, password, location, reason, visible, certify, timestamp, title, author, subject, keywords, conffile)
prepare_signature(input, output, password, location, reason, visible, certify, signername, certsn, conffile)
add_metadata_prepare_signature(input, output, password, location, reason, visible, certify, signername, certsn, title, author, subject, keywords, conffile)
create_signature(hash, timestamp, conffile)
apply_signature(output, signature)
add_ltv(input, output, conffile)
verify(input, conffile)
The test directory of the installation includes a couple of examples that show how to use these functions and what return values to expect.
<?php $inputPDF = "/usr/local/mypdfsigner/tests/example.pdf"; $outputPDF = "/tmp/example-signed-php.pdf"; $password = ""; # if non empty document will also be encrypted $location = "PHP Location"; $reason = "PHP Reason"; $visible = TRUE; $certify = TRUE; $timestamp = TRUE; $title = "PHP Title"; $author = "PHP Author"; $subject = "PHP Subject"; $keywords = "PHP Keywords"; $confFile = "/usr/local/mypdfsigner/tests/mypdfsigner.conf"; $signResult = mypdfsigner_add_metadata_sign($inputPDF, $outputPDF, $password, $location, $reason, $visible, $certify, $timestamp, $title, $author, $subject, $keywords, $confFile); echo $signResult . "\n"; $verifyResult = mypdfsigner_verify($outputPDF, $confFile); echo $verifyResult . "\n"; ?>
require 'mypdfsigner' include MyPDFSigner inputPath = "/usr/local/mypdfsigner/tests/example.pdf" outputPath = "/tmp/example-signed-ruby.pdf" password = "" # if non empty document will also be encrypted location = "Ruby Location" reason = "Ruby Reason" visible = true certify = true timestamp = true title = "Ruby Title" author = "Ruby Author" subject = "Ruby Subject" keywords = "Ruby Keywords" confFile = "/usr/local/mypdfsigner/tests/mypdfsigner.conf" signResult = mypdfsigner_add_metadata_sign(inputPath, outputPath, password, location, reason, visible, certify, timestamp, title, author, subject, keywords, confFile) puts signResult verifyResult = mypdfsigner_verify(outputPath, confFile) puts verifyResult
import mypdfsigner inputPath = "/usr/local/mypdfsigner/tests/example.pdf" outputPath = "/tmp/example-signed-python.pdf" password = "" # if non empty document will also be encrypted location = "Python Location" reason = "Python Reason" visible = True certify = True timestamp = True title = "Python Title" author = "Python Author" subject = "Python subject" keywords = "Python keywords" confFile = "/usr/local/mypdfsigner/tests/mypdfsigner.conf" signResult = mypdfsigner.add_metadata_sign(inputPath, outputPath, password, location, reason, visible, certify, timestamp, title, author, subject, keywords, confFile) print signResult verifyResult = mypdfsigner.verify(outputPath, confFile) print verifyResult
Note that although the path to the configuration file can be passed as an argument of the sign function, that approach is not recommended if using PKCS#11 key stores. Instead it is recommended that the configuration file is saved to the default location (/usr/local/mypdfsigner/mypdfsigner.conf) and an empty argument is passed to the sign function. This has the benefit that the registration of the PKCS#11 engine happens at startup time (i.e., when the web server starts) and the cleanup happens at shutdown time (when the web server shuts down). This issue is not relevant if using the command line or if using a PKCS#12 key store.